Reading Time: 4 minutes
Reading Time: 4 minutesIntroduction
One of the critical challenges organizations face while building a new AI platform is considering whether the platform meets the data sovereignty and data protection regulations of the operating country. This is more crucial now than ever, as most organizations are amid their cloud adoption journeys.
In this blog, I will explain:
- What is data sovereignty?
- Why is data sovereignty essential?
- What are the business and architectural challenges in meeting data sovereignty regulations?
- How does Refract, the Insight Designer module of the Fosfor Decision Cloud, help clients build AI platforms in line with data sovereignty requirements?
What is data sovereignty?
Data sovereignty is a concept wherein a nation or legal jurisdiction possesses the prerogative and entitlement to oversee and manage data originating within its confines. Under this principle, the government holds the authority to administer the acquisition, retention, manipulation, and dissemination of data that has its origins within the geographical boundaries of the nation.
For example, in the case of a multi-national corporation, operations would typically span countries with varying levels of data regulations, and in some cases even require the compute cycles to be executed locally within the country.
Let’s assume a client has operations across Europe, wherein all the Schengen countries within Europe except for one country (For e.g., country 3) can share the same infrastructure, storage, and compute. In this case, since country 3 has a stricter data sovereignty regulation, data collected, stored, or processed locally cannot be accessed outside country 3.
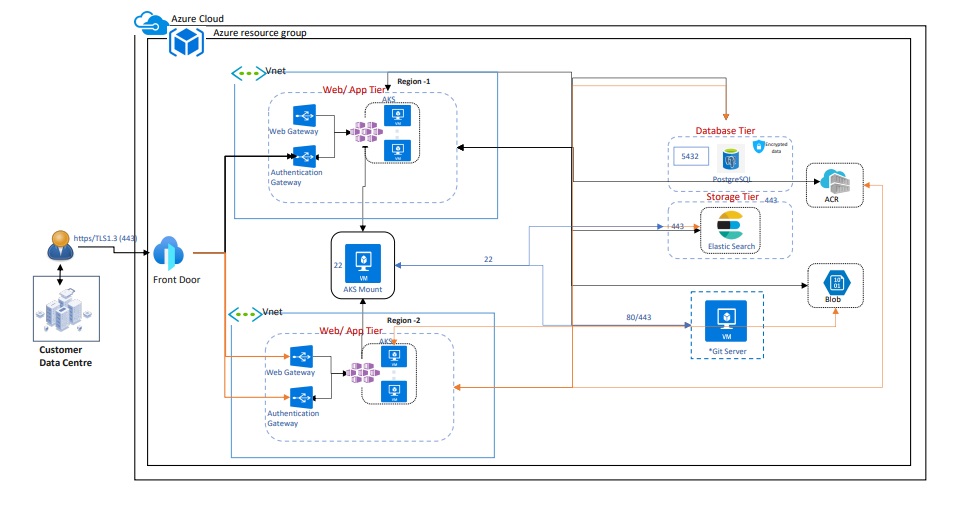
If an enterprise has operations in three countries, where country 1 and country 2 are Schengen countries governed by the same data regulations, and country 3 has stricter laws that mandate all the data storage, compute, and consumption happen locally in the country, users will have to adapt a distributed architecture. Let’s assume we have three users; User 1 and 2 belong to country 1 and 2, respectively, while user 3 belongs to country 3. As illustrated in Figure 1 below, while the workloads of user 1 and 2 could be pushed to a shared infrastructure, user 3’s workload should be pushed to a dedicated infrastructure.
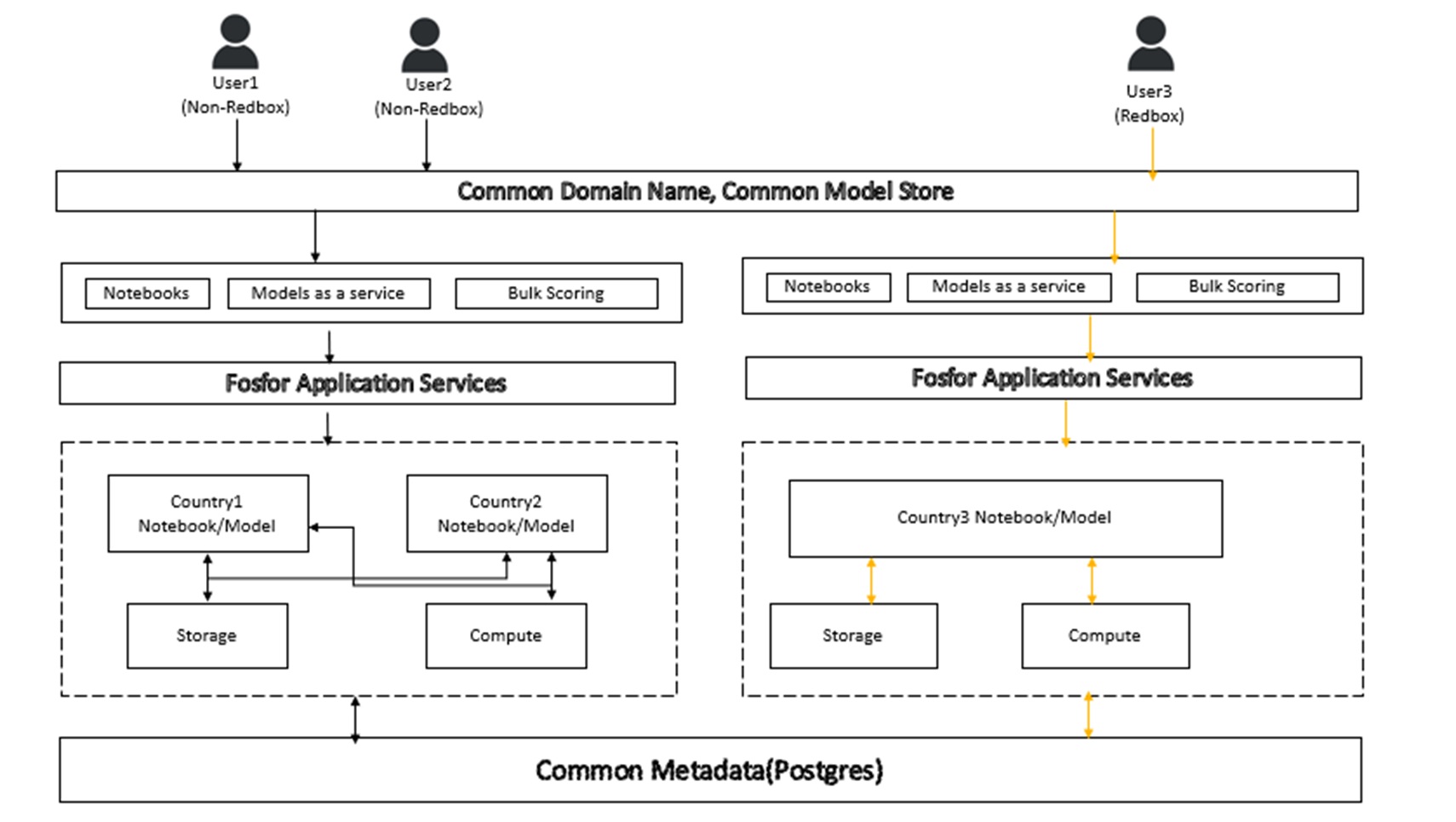
Figure 1: Shared & dedicated infrastructure architecture
Why is data sovereignty essential?
As enterprises generate vast volumes of data via various channels such as eCommerce, mobile devices, and social media, there is a considerable responsibility for safeguarding this massive data collection. With an evolving presence in laws and regulations across nations, data sovereignty ensures that sensitive data–such as personal information or trade secrets–aren’t easily abused by cybercriminals.
Data sovereignty also provides companies willing to comply with local regulations, a competitive advantage over peers. This is particularly true as compliance demonstrates a commitment to protecting customer data, building trust with customers, and gaining an edge over those who disregard data security.
It is essential to note that enterprises need to ensure they meet the data sovereignty requirements of the countries they operate in, or else they face the risk of huge penalties and reputational risk.
What are the business and architectural challenges in meeting data sovereignty regulations?
Meeting data sovereignty regulations poses significant challenges for businesses operating in an era where data has become a global currency. These regulations, which require data to be stored and processed within specific geographic boundaries, have far-reaching implications for organizations of all sizes and industries. In this increasingly interconnected world, businesses navigate a complex web of legal, operational, and compliance issues. This article delves into the business challenges associated with data sovereignty regulations, shedding light on the critical considerations and strategies needed to effectively address these concerns while staying competitive in a data-driven economy.
The following are some of the challenges associated with meeting data sovereignty regulations:
- Data localization: Regulations often require data to be stored within specific geographic boundaries. This can be costly as it may necessitate setting up local data centers or using cloud providers with data centers in the relevant region.
- Data management: Managing data in compliance with various regulations can be complex and resource-intensive. Businesses must implement robust data governance, encryption, and access control mechanisms.
- Compliance costs: Achieving compliance often involves substantial financial investments in technology, legal counsel, and compliance audits, which can strain a company’s budget.
- Legal and regulatory complexities: Data sovereignty laws and regulations can vary widely from one jurisdiction to another. Understanding and navigating this legal landscape can be daunting, especially for businesses with an international presence.
- Business disruption: Complying with data sovereignty regulations can lead to disruptions, including service downtime or changes in data processing practices, which may impact customer experience and revenue.
- Data transfer restrictions: Regulations can limit the cross-border transfer of data, which can hinder global business operations and disrupt supply chains.
- Data security: Businesses must implement robust security measures to protect data within specific regions, as breaches can result in severe penalties and reputation damage.
- Vendor selection: Choosing the proper data storage and processing vendors that comply with local regulations can be challenging, as not all cloud service providers may have a presence in every region.
- Privacy concerns: Meeting data sovereignty requirements often involves addressing privacy concerns and ensuring customer data is handled per local privacy laws.
- Data portability: Regulations may require businesses to enable data portability, allowing individuals to move their data between service providers, which can be technically challenging.
- Contractual obligations: Businesses may need to renegotiate contracts with vendors and customers to ensure compliance with data sovereignty laws, which can be time-consuming and costly.
- Risk management: Companies must develop risk mitigation strategies to address the potential legal and financial risks associated with non-compliance.
- International expansion challenges: Expanding into new markets means dealing with additional data sovereignty regulations, creating complexities for global expansion strategies.
- Data residency and backup: Ensuring the data is always accessible and recoverable, even when subjected to local regulations, can be a considerable technical challenge.
- Monitoring and reporting: Meeting compliance often requires continuous monitoring and reporting on data handling practices, which can be resource-intensive.
- Employee training: Businesses must ensure that employees are aware of and trained in compliance with data sovereignty regulations, which may require ongoing education programs.
Navigating these challenges is essential for businesses to thrive in a data-driven world while complying with the complex and ever-evolving landscape of data sovereignty regulations.
Here are some architectural approaches that can help companies to mitigate these challenges:
Option 1: A separate cluster for each country.
Option 2: A common cluster for a group of countries and a separate cluster for countries with stricter regulations, with a separate domain name and separate metadata.
Option 3: A common cluster for a group of countries and a separate cluster for countries with stricter regulations, with a common domain name and common metadata.